- 1st place: VuwCTF Grumpy C
- 2nd place: w2d
- 3rd place: [VuwCTF]BAkingBRead
- 1st place: sigsegv
- 2nd place: VuwCTF Aterlone
- 3rd place: VUWCTF stegfan19274
- 1st place: Cale
- 2nd place: Anthony
- 3rd place: logebear555
CHALLENGE OVERVIEW
Unlike previous years the NZCSC will consist of a single Capture-The-Flag (CTF) competition, held online from July 11 to July 17.
The CTF will consist of multiple challenges. Participants will compete to find hidden "flags" embedded within each challenge.
The topics that the challenges cover include, but are not limited to:
- Cryptography
- Steganography
- Web Application Security
- Forensic
RESOURCES
Tools
The tools that can be used for solving sepecific topics are listed below, but not limited to:
- Cryptography: dcode.fr
- Steganography: Audacity, GIMP
- Networking: Wireshark
- Forensic: hexdump, HexEditor e.g., Visual Studio Code with Hex Editor Extension, Volatility, GDB
- General Tools: Kali Linux, CyberChef
Linux and Python Tutorial
Cryptography Tutorial
Forensic Tutorial
Interesting External Channels
- John Hammond: https://www.youtube.com/c/JohnHammond010/videos
- HackerSploit: https://www.youtube.com/c/HackerSploit/videos
- Cryptography for Everybody: https://www.youtube.com/c/CrypTool2/videos
- IppSec: https://www.youtube.com/c/ippsec/videos
- Networks - David Bombal: https://www.youtube.com/c/DavidBombal/videos
- Forensics - DFIRScience: https://www.youtube.com/c/DFIRScience/videos
SOLUTIONS
New Zealand Cyber Security Challenge
What is NZCSC?
NZCSC is the New Zealand Cyber Security competition which is held annually. The competition is open to all New Zealanders and is designed to promote interest in cyber security and encourage students to pursue careers in this field.
What is a CTF?
A CTF (Capture The Flag) is a cyber security exercise consisting of multiple puzzles/challenges. Each puzzle has a flag hidden somewhere and the challenge is to find the flag. The flag usually is a sequence of alphanumeric characters. Once you find a flag you get some points. The objective is the find as many flags as possible and collect points.
Who can participate in NZCSC?
Anyone in New Zealand can participate in NZCSC.
Do I participate solo or in teams?
You only participate solo.
Each participant competing individually will be assigned to one of the following ranked categories:
- Open/Industry
- University
- High School
Is there a participation fee?
No. There is no fee to participate.
Can I win prizes?
Yes! For each category, the prizes for the winners are as follows:
- 1st place: 400 NZD
- 2nd place: 200 NZD
- 3rd place: 100 NZD
Great! Where do I sign up?
Follow the link on homepage to submit your expression of interest and we will keep you posted once registration opens.
CROW-NZ's First Cyber Security Lab

Established in 2012, CROW is a research group located in the Department of
Computer Science at The University of Waikato.
With the emergence of cloud computing technologies and prevalent mobile device usage, we are
witnessing the diminishing effectiveness of traditional cyber security approaches such as perimeter
defence, intrusion detection and infrastructure hardening.
To address this, CROW focuses on six major themes: Provenance, User-Centricity, Visualisation,
Economics, Hardware, and Tools & Datasets. Together, these six themes enable the return of control
of data to users, thereby reducing reliance on third-party vendors or trust relationships commonly
found in most cyber security contracts today
HISTORY
NZCSC 2024 Winners
Grand Prize Winner: Jamie McClymont and Thomas Hobson
Grand Runner-up: Michael Young and Aaron Rumpler
Round 1 Category Winners:
- High School Category: Tane Haines, Ture Hansson, Oscar Horne
- Tertiary Category: Michael Young, Aaron Rumpler
- Industry/Open Category: Elliott Lawrence, Jakub Sawicki
Round 2 Category Winners:
- High School Category: Fionn Cassidy, Ivan Shabashev
- Tertiary Category: Jess Churchill, Avocado Rider
- Industry/Open Category: Jamie McClymont, Thomas Hobson
Round 2 Runner-up:
- Secondary Category: Tane Haines, Ture Hansson, Oscar Horne
- Tertiary Category: Michael Young, Aaron Rumpler
Side Challenge Top 3 Winners:
- Jake Nicholson
- Aidan Dunn
- Jack Crenfeldt
NZCSC 2023 Winners
Grand Winners: Cale Budd, Josh Hogan, Sam Hogan
Grand Runner-up: Charlotte MacKenzie, Jamie McClymont
Round 1 & 2 Winners:
Secondary Category:- Elijah Michel
- Thomas Jackson
- Alex Berry
- Ava Rider
- James Churchill
- Thomas Hobson
- Caleb Butcher
- Yek Tham
- Austin Chamberlain
Round 1 & 2 First Runner-up:
Secondary Category:- Elliott Bell
- Maxwell Robati
- Toby Connor-Kebbell
- Jonty Morris
- Sam Redmond
- Oliver Wright
Round 1 & 2 Second Runner-up:
Secondary Category:- Joel Bannister
- Lev Petersen
- Theo Keith
- Ethan Doughty
- Jack Gong
- John C
Challene Solvers
- Medium Challenge 8 First Solver: Bert Downs, Rowan Thorley, Alexander Stokes
- Medium Challenge 10 First Solver: Anthony Chilcott-Parker
- Medium Challenge 11 First Solver: Cale Budd, Josh Hogan, Sam Hogan
- Medium Challenge 12 First Solver: Cale Budd, Josh Hogan, Sam Hoga
High School Special Prize
- First Solver Challenge 2: Aaron Moore, Gavith Dharmasena, Jack Li
- Second Solver Challenge 1: James de Hair, Harrison Welford, William Robbers
NZCSC 2022
WHAT HAPPENED?
The 2022 NZ Cyber Security Challenge was held online with Round 0, Round 1 and 2 were on-campus.
- Waikato x Cardiff winners -
Congratulations to the winners of Waikato x Cardiff round. The Waikato University winner is DoingGood. The Cardiff University winner is heartburn.
- Round 1 and 2 winners -
Grand Prize Winner, 1500 NZD : Covid_Brain
Round 1 Category Winner, 750 NZD
- HighSchool Category: WHS's finest
- Tertiary/University Category: Unluggy Uce
- Industry/Open Category: The Prototype Polluters
- HighSchool Category: stAk
- Tertiary/University Category: Unluggy Uce
- Industry/Open Category: Covid_Brain
- HighSchool Category: Team 3
- Tertiary/University Category: The Pi Guys
- Industry/Open Category: The Prototype Polluters
- HighSchool Category: BeefStew
- Tertiary/University Category: NightmareRats
- Industry/Open Category: anthonycp
- Medium and Hard Challenges -
Medium Challenges, 75 NZD- Challenge 4: Team 6
- Challenge 9: SaladPants
- Challenge 11: anthonycp
- Challenge 2: The Interns
- Challenge 7: Covid_Brain
- Challenge 12: The Prototype Polluters
NZCSC 2021
WHAT HAPPENED?
The 2021 NZ Cyber Security Challenge was held online with Round 0, Round 1 and 2 were on-campus.
Grand Prize Winner - Sponsored By Bhojraj Parmar: Rhys Davies
Round 2 Category Winner
- HighSchool Category: Andrew Rider
- Tertiary/University Category: Cale Budd
- Industry/Open Category: Rhys Davies
- HighSchool Category: Misha Pavlov
- Tertiary/University Category: Sam Redmond
- Industry/Open Category: Grady Hooker
- HighSchool Category: Finn Robinson
- Tertiary/University Category: Ethan Mckee-Harris
- Industry/Open Category: Brendan Laing
Medium Challenges
- Challenge 6: Logan Krippner
- Challenge 7: Kushan Fernando
- Challenge 13: Sam Redmond
- Challenge 15: Logan Warner
- Challenge 8: Jamie McClymont
Notice regarding NZCSC 2021: After the culmination of NZCSC'21 it was brought to our attention that some challenges were plagiarized from sources on the internet. The NZCSC organisers reported this to the employer of the person who created and submitted the challenges to be used in NZCSC. The employer took swift and strictest possible action for the misconduct. The NZCSC values integrity above everything else and the team was deeply saddened with the discovery. We apologise to all NZCSC'21 participants for this oversight and assure everyone that we have now put measures in place to ensure this does not happen again.
NZCSC 2020
WHAT HAPPENED?
The 2020 NZ Cyber Security Challenge was held online with Round 0, Round 1 and a purple team challenge
all held online
Grand Winner: Jamie McClymont
Category Winners
- HighSchool Category: Technocoder(Zhiyuan Qi)
- Tertiary/University Category: Dast(Daniel Stokes)
- Industry/Open Category: Jamie McClymont
- Dast (Daniel Stokes)
- Tomais Williamson
- Jamie McClymont
- Logan Krippner
- Technocoder(Zhiyuan Qi)
- ZerOne (Sam Redmond)
- Samdaman (Sam Hogan)
- Fromage (Joshua Hogan)
- Michael Jang
- RavSS (Ravjot Singh Samra)
Medium Challenges
- Challenge 4: Fromage (Joshua Hogan)
- Challenge 5: Toby Heitland
- Challenge 7: Gittarackur (Ryo Sugiyama)
- Challenge 8: Fromage (Joshua Hogan)
- Challenge 10: Jamie McClymont
- Challenge 11: Jamie McClymont
- Challenge 12: Jamie McClymont
NZCSC 2019
FIRST PLACE
Team 'The Password Inspectors' - Jamie McClymont, Rhys Davies.

WHAT HAPPENED?
Congratulations to all the Cyber Security Challenge competitors of 2019. This year, the challengers took on the Internet of Things with the focus on - forensics, reverse engineering, steganography, web-application security and cryptography.
RUNNER-UP OF TERTIARY CATEGORY
Now UC Me (Joshua & Sam Hogan, University)
WINNER OF SECONDARY CATEGORY
Thonking (Cameron Li & Jason Xu)
RUNNER-UP OF SECONDARY CATEGORY
Arrays start at 1 (Ethyn Gillies & Marshall Patty)
RUNNER-UP OF SECONDARY CATEGORY
Frozen Orange (Orion Edwards & Thilanka Priyankara)
RUNNER-UP OF INDUSTRY CATEGORY
Gradyhooker (Grady Hooker).
NZCSC 2018
FIRST PLACE
Team Elliptic Curveballs - Logan Krippner, Jacob Cheatley and Michael Jang.

Women's Technical Challenge Champions
Team Octocats - Jamie McClymont and Abigail Koay
Drone challenge winners
Team UniHack - Rajat Rokhade, Debac Manikandan and Arnav Gogia
WHAT HAPPENED?
The NZ Cyber Security Challenge 2018 (NZCSC'18) hovered into action with a drone challenge for Round 1
& 2 contestants at the University of Waikato campus.
Challengers tested their hacking skills as they attempted to take charge of a drone controlled by a
host's smartphone and intercept photos taken by the drone's camera. Prizes were awarded to the
successful hackers.
NZCSC'18 action also included training sessions with some of the best, opportunities to kickstart a
cyber security career at the job fair and talks by some of the movers and shakers in the industry.
Round 0 online qualifying round took place from June 18-29, with the top 150 moving on to Rounds 1 and
2 on July 14 at the University.
CSC 2017
FIRST PLACE
2017 challenge known for Challenge Winner Repeat Performance .
It was a repeat performance by
the overall champions team Arcton, Nathaniel Watson, Jeremy Symon and Grady Hooker took out last
year's Challenge.
Representing industry, they walked away with a cheque for $2500 and
NetHui fellowships. Jeremy is currently doing a Masters of Computer Science at Waikato and working at
Gallagher, and Grady and Nathaniel are former Waikato Computer Science students now working in the
computer science industry.

RUNNERS UP
Overall runners-up 418ShortAndStout - Michael Robertson and Brent Vollebregt - placed top in the
tertiary division and took home $1800.
Top performers in the high school division after Rounds 1 and 2, SQL Sharks twins Sam and Josh Hogan
also took out first place in the new Policy Round. Contestants were tested on responsible disclosures,
asked to critique a really badly-written cyber policy, and suggest incident response next steps for a
fictitious event.
The winning team from the industry division after Rounds 1 and 2 were Jack Haystead, Daniel Tebbutt
and Declan ter Veer-Burke. They took home a cheque for $1800.
WHAT HAPPENED?
NZCSC'17 hit all the right keys with VIPs from the Government Communications Security Bureau (GCSB)
and INTERPOL attending. GCSB director Andrew Hampton told the Challengers it wasn't long ago that
people were saying cyber security should be on the agenda but now the agenda is cyber security.
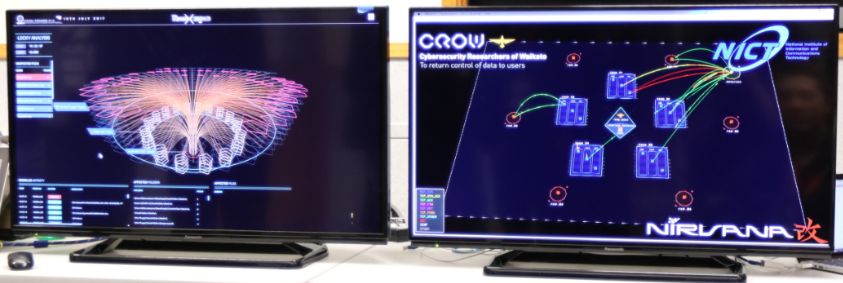
Although, In this year's Challenge CROW collaborated with Japan's National Institute of
Communications and Information Technology ( NICT ) to up the ante in the visualisation of
the attack and defend networks of the competition. CROW member Cameron Brown worked with Koei Suzuki
to customise the NIRVANA Kai visualisation to show network traffic between the Round 3 servers. The
collaboration is mutually beneficial as NICT will utilise CROW technology in the future. NICT supply
the visualisations for Japan's largest cyber security competition SECCON.
CSC 2016
FIRST PLACE
Team Name: Hodor (462,250 points)
Team Members: Sjoerd de Feijter, Matthew Stringer, Vladimir Petko
Industry category team, representing Gallagher Group
RUNNERS UP
First Runner-Up
Team Name: Solo Team(406,160 points)Team Members: Michael Robertson, 17 years old,
Secondary School Category team, representing Cambridge High School.
Second Runner-Up
Team Name: Arcton(386,300 points)Team members: jeremy Symon, Nathaniel Watson, Grady Hooker
Tertiary category team, representing University of Waikato Faculty of Computing And Mathematical Sciences
WHAT HAPPENED?
Due to the popularity of the competition in 2015, we introduced an online qualifying round, Round
Zero. 267 participants registered for Round Zero and attempted the challenges between the 17 June -
1st July, after which the Top 150 were chosen to attend the competition on the 14 and 15 July.
Participants competed in two rounds: Round One, a capture-the-flag style challenge and Round Two, a
Red team vs. Blue team game where the Blue teams had to defend their vulnerable servers from attacks
from the Red teams, which consisted of an Industry Professional from Gallagher and two CROW members.
CSC 2015
FIRST PLACE
Team Name: Ter B
RUNNERS UP
First Runner-Up
Team Name: DoubleMCSecond Runner-Up
Team Name: Kanye4PrezWHAT HAPPENED?
NZCSC'15 was open to all of New Zealand and participants were split into 3 categories: Secondary,
Tertiary, and Industry/Open.
The competition had 2 rounds: Round 1 was a capture-the-flag style challenge. Round 2, open to the top
5 teams of Round 1, was a Red team vs. Blue team style challenge where 5 Blue teams defended their
systems against the Red team, which included Industry professionals from Insomnia Security and PWC
Digital.
CSC 2014
The first instalment of the Cyber Security Challenge was open to University of Waikato students only.
CSC'14 had a single round - a capture-the-flag style challenge where the students participants solved
challenges to acquire flags. The event served its purpose: to gauge students' interest in a Cyber
Security-themed competition. Over 70 students registered, attended the training and paticipated in the
competition, which encouraged the organisers to plan the next CSC.